Wavelet-based Steganography (JPEG2000)
In addition to DCT, images can be processed with
discrete
wavelet transformation DWT. Wavelet is used in
JPEG2000 compression to perform the
transformation. The wavelet
transformation is followed by quantization and
encoding stages.
Various algorithms and approaches are used in
embedding process which takes place after the
wavelet transformation of the image in order to
hide the secret message in it. After applying
the discrete
wavelet transform (DWT) on the original image
and getting the wavelet coefficients, the
wavelet coefficients are changed according to
the embedded data. Finally, inverse wavelet
transform (IDWT) is applied to get the
steganographed image.
we will discuss a method of steganography
technique based on DWT transform whish was
proposed in the reference shown below. The method has ability to hide
secret message in a digital image. The secret
message is embedded into the image by changing
wavelet coefficients. The quality of the stego
image of this method is very close to that of
the original one.
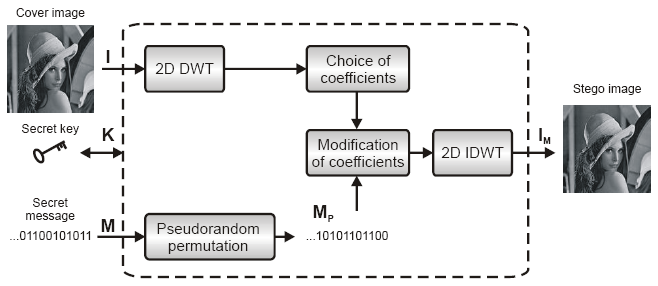
Embedding process contains two-dimensional
discrete wavelet transformation of cover image,
permutation of secret message, modification of
transformation coefficients and finally inverse
2D-DWT of modified coefficients. Inputs of
embedding process are cover image and secret
message. Output of this process is stego image. Secret key contains information about
choice of DWT transformation coefficients and
permutation random vector. Before modification
of coefficients, pseudorandom permutation of the
secret message is used for increasing security
of embedded message, see the figure shown below.
The
following form expresses the embedding process,
where m (x) represents the secret message’s bit and i (x)
represents the
DWT coefficient. Modified
DWT coefficient can
be expressed in the following form: 
Where
a
is a real number.
The
extraction of secret message from the
steganographed
image will be done by comparing the selected DWT
coefficients of the steganographed and original image. The
comparison operation can be expressed in the
following form:

Reference:
• STEGANOGRAPHY BASED ON DWT TRANSFORM, by
Rastislav Hovančák, Peter Foriš, Dušan Levický. |

