|
Information Hiding
and its Applications
Steganography and Watermarking
A detailed look at Steganography
◦ Text Steganography
◦ Hypertext Steganography
◦ Audio Steganography
◦ Image Steganography
◦ Steganography in Open System
Image Steganography Techniques
◦ Spatial Domain LSB Insertion
◦ Masking and Filtering
◦ DCT-based Steganography
◦ Wavelet-based Steganography
How to Detect Steganography
◦ Blind Detection
◦ Analytical Detection

|
DCT-based Steganography
The
Discrete Cosine Transformation (DCT) is used by
the JPEG compression algorithm, therefore the
DCT-based steganography methods apply only for
jpeg image format. The DCT transformation is
used by the JPEG algorithm to transform
successive 8x8 pixels blocks of the image, into
64 DCT coefficients each. Each 8x8 pixels block
of the image will be transformed into an 8x8
DCTs block by the use of the relation shown
below. Each DCT coefficient F(u , v) of an 8x8
block of image pixels f(x , y) is given by:
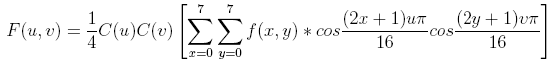
where
C(x) = 1/√2 when x equals 0 and C(x) = 1
otherwise. After calculating the coefficients,
the following quantizing operation is performed:
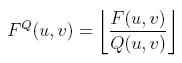
where Q(u, v) is a 64-element quantization
table. A simple code algorithm to hide a message
inside a JPEG image could look like this:

Although a modification of a single DCT will
affect all 64 image pixels, the LSB of the
quantized DCT coefficient can be used to hide
information. Lossless compressed images will be
suspectible to visual alterations when the LSB
are modified. This is not the case with the
above described method, as it takes place in the
frequency domain inside the image, instead of
the spatial domain and therefore there will be
no visible changes to the cover image.
References:
• Steganography and Steganalysis, by J.R.
Krenn, January 2004. |

