|
About DCT-Based Mod4 Method:
We
can make an innocent image a communication
channel by embedding a message within the image.
The image will represent a hidden communication
channel, where no one knows what it contains
except the sender and the intended receiver.
Many image-based steganographic methods have
been invented in the spatial and DCT domains. In
this project, we focus on the Mod4 algorithm as
one of the well-known algorithms in the DCT
domain.
The
Mod4 algorithm was developed by Wong, Qi, and
Tanaka [1]. Each 8x8 block of qDCT coefficients
is divided into 16 contiguous GQCs, where each
GQC is composed of 2x2 qDCT coefficients. The
GQCs are tested to identify the valid GQCs (vGQC).
The vGQC must meet two conditions considering
the magnitudes of the coefficients and their
number, where these conditions are donated by
the values of Φ1, Φ2, τ1, and τ2 parameters.
The
Modulo operation of 4 is used as a hash
function. Applying The Modulo operation to a
vGQC will produce 2 Bits. To embed 2 Bits in a
vGQC, the sender needs to modify its
coefficients accordingly, so when the receiver
hashes the modified vGQC, the secret message of
2 Bits will be obtained. The modifications
applied to the vGQC are restricted to the
shortest route modification scheme SRM developed
by Wong et al. [1]. The SRM is based on two
principles; firstly, the modifications applied
to the coefficients should be minimal; secondly,
the modifications should be applied to the
larger coefficient first. |
|
What is the Magic Triangle ?: |
|
 |
|
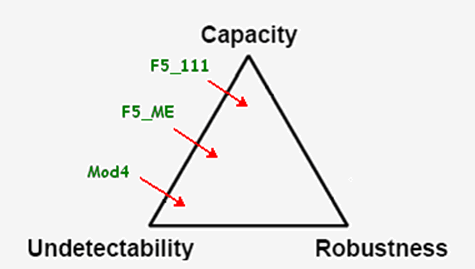
In the
field of information hiding, there is a visual
requirements model called the Magic Triangle,
proposed by Johnson et al. [2]. Each corner, in
the Magic Triangle, represents a basic
requirement; undetectability, robustness to
attacks, and the insertion capacity. This visual
model is convenient for presenting the balance
between the three desirable requirements. It
shows that these requirements cannot be made
perfect at the same time; when we get closer to
a corner, we move away from another corner. As a
clarification, there is a trade-off between the
insertion capacity and the robustness against
attacks. It is not possible to have high
insertion capacity and high robustness to signal
modifications at the same time. In other words,
the presence of large embedded data makes the
carrier medium vulnerable to signal modification
attacks.
Steganography pays much more attention to
insertion capacity rather than robustness
against attacks, while watermarking has a great
interest in robustness against signal
modifications since it aims to protect the
ownership of a medium. On the other side,
steganographic algorithms should not cause any
perceptible distortion and have to be
statistically invisible, so it should be very
difficult to prove the presence of a hidden
message. In the steganography, we aim to hide a
large message using an undetectable way, but we
cannot realize a perfect undetectability and a
large capacity at the same time. |
|
Comparing Mod4 with F5 from The perspective of
the Magic Triangle: |
|
 |
|
The determination of the approximate locations
of Mod4 and F5 algorithms is the result of a
comparative study completed in chapter 4 of the
Ms thesis of Al Chamaa [3]. The resulting Magic
Triangle shows how Mod4 stands compared to F5.
In other words, it shows how each algorithm
satisfies each requirement compared to the other
one. |
|
In the following, we will show some comparative
results taken from the MS thesis we mentioned
above [3]. These results concern the insertion
capacity, stego image quality, and statistical
distribution: |
|
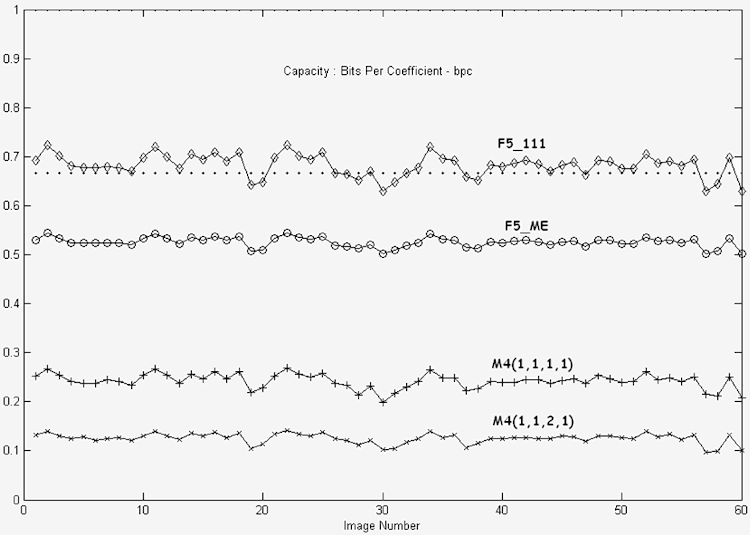
The Insertion Capacity of Mod4 Compared to F5: |
|
The following graph shows the bpc values for 60
jpeg images. |
|
 |
|
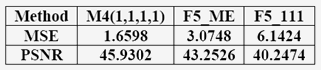
The Stego Image Quality of Mod4 Compared to F5 -
(MSE, PSNR): |
|
The following table presents the average values
for 60 jpeg images. |
|
 |
|
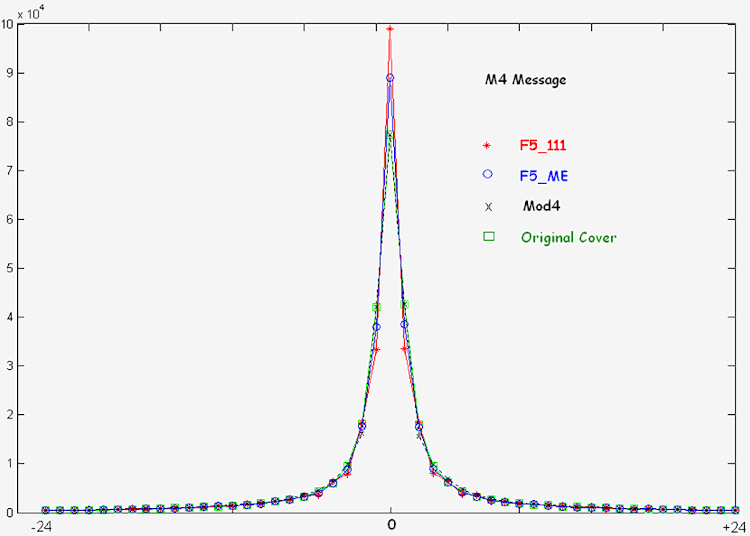
The Resulting Histogram of Mod4 Compared to F5: |
|
The following graph shows the resulting
histograms. The inserted message corresponds to
the maximum capacity provided by Mod4. |
|
 |
|
References: |
|
[1]:
"A DCT-based Mod4 Steganographic
Method" by Wong et al., 2007.
[2]: "Information Hiding: Steganography
and Watermarking Attacks and Countermeasures".
by Johnson et al., 2001.
[3]:
"Cryptography and Steganography in Digital
Images" by Al Chamaa, 2009. |
|