|
Information Hiding
and its Applications
Steganography and Watermarking
A detailed look at Steganography
◦ Text Steganography
◦ Hypertext Steganography
◦ Audio Steganography
◦ Image Steganography
◦ Steganography in Open System
Image Steganography Techniques
◦ Spatial Domain LSB Insertion
◦ Masking and Filtering
◦
DCT-based Steganography
◦
Wavelet-based Steganography
How to Detect Steganography
◦ Blind Detection
◦ Analytical Detection

|
Image Steganography Techniques
Spatial domain LSB insertion
Usually 24-bit or 8-bit files are used to store
digital images. The former one provides more
space for information hiding; however, it can be
quite large. The colored representations of the
pixels are derived from three primary colors:
red, green and blue. 24-bit images use 3 bytes
for each pixel, where each primary color is
represented by 1 byte. Using 24-bit images each
pixel can represent 16,777,216 color values. We
can use the lower two bits of these color
channels to hide data, then the maximum color
change in a pixel could be of 64-color values,
but this causes so little change that is
undetectable for the human vision system. This
simple method is known as Least Significant Bit
insertion. Using this method, it is possible to
embed a significant amount of information with
no visible degradation of the cover image.
The following Figure shows the insertion process.
Several versions of LSB insertion exist. It is
possible to use a random number generator
initialized with a stego-key and its output is
combined with the input data, and this is
embedded to a cover image. For example in the
presence of an active warden it is not enough to
embed a message in a known place (or in a known
sequence of bits) because the warden is able to
modify these bits, even if he can’t decide
whether there is a secret message or not, or he
can’t read it because it is encrypted. The usage
of a stego-key is important, because the
security of a protection system should not be
based on the secrecy of the algorithm itself,
instead of the choice of a secret key, the figure
below shows the process.
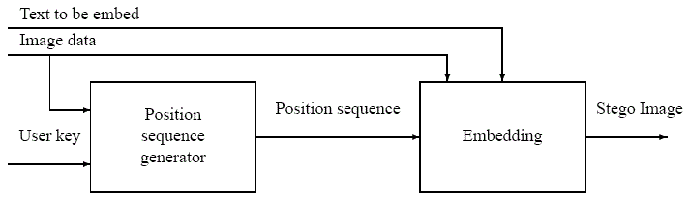
The
LSB inserting usually operates on bitmap images.
The embedded data cannot be considered as a
watermark, because even if a small change occurs
in a picture
(cropping, lossy compression, and color
degradation) the embedded information will be
lost although the change which is occurred
during the embedding process is invisible.
Finally, the LSB insertion method is a very
popular method because of its simplicity. But
the main drawback of this technique is that its
weakness against some attacks such as lossy
compression, where the hidden information will
be lost.
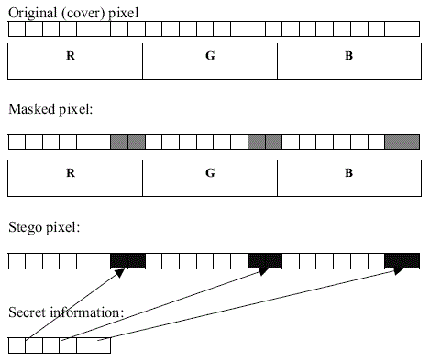
Masking and filtering Steganography
Masking and filtering techniques are mostly used
on 24 bit and grey scale images. Masking images
entails changing the luminance of the masked
area. The smaller the luminance change, the less
of a chance that it can be detected. In other
words Masking and filtering techniques hide
information by marking an image in a manner
similar to paper watermarks.
Because watermarking techniques are more
integrated into the image, they may be applied
without fear of image destruction from lossy
compression. By covering, or masking a faint but
perceptible signal with another to make the
first non-perceptible, we exploit the fact that
the human visual system cannot detect slight
changes in certain temporal domains of the
image.
Here it is good to remember the difference
between watermarking and steganography; Digital
watermarks may include information as copyright,
ownership, or license. In digital watermarking,
the object of communication is the cover. But in
steganography, the object of communication is
the hidden secret message.
To perform steganography within an image, the
luminance of the masked area is increased by 15
percent. The luminance must be changed by a
smaller percentage, so the mask would be
undetected by the human eye. Now we can use the
image to hide plaintext or encoded information.
Masking is more robust than LSB insertion with
respect to compression, cropping, and some image
processing. Masking techniques embed information
in significant areas so that the hidden message
is more integral to the cover image than just
hiding it in the “noise” level. This makes it
more suitable than LSB with lossy JPEG images.
Reference:
• STEGANOGRAPHIC METHODS, by József LENTI , June
2000. |

